|
To send some information to another user who has MPGP installed, right click on their nick, and select MPGP Crypto Operation.
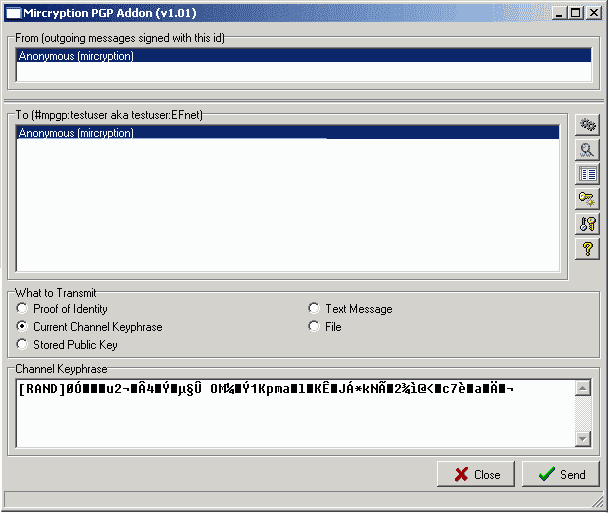
This will bring up the main MPGP transmission dialog. If MPGP is not already in memory, there will be a slight delay as the random number generator is seeded.
Select the Transmission Type from the "What To Transmit" radio group.
Proof of Identity - MPGP provides an automatic protocol for authenticating yourself to someone who already has one of your permanent (non-anonymous) keys.
| • | You can only authenticate yourself using a non-anonymous key that the recipient already has. To do this, select your identity as one of the non-anonymous entries in the FROM box. [Reminder: you can generate non-anonymous keys using the PGP Key tool, the button with two keys on it]. You can then enter some additional text in the Contents box, which will be shown if you are properly authenticated. |
| • | In the To field you can select either anonymous or a known key for the recipient. The process for authentication occurs automatically as follows: |
| • | Your mirc will acquire the other persons anonymous key if necesary. |
| • | Your mirc will then request a random proofstring from your intended recipient. |
| • | Your recipient will generate a string with a random component and the current date and time, along with your nick and the recipient's nick, and send that to your mirc. |
| • | Your mirc will then encrypt that string and sign it with your non-anonymous key and return it to the recipient. Your signature is unique and cannot be spoofed by others. |
| • | The recipient mirc will decode the signed signature and make sure it is valid and contains the same string that it initially sent out. The proofstring ensures that you cannot fake your identity by capturing and replaying previous proofs. Because signing something with a non-anonymous key requires the signer to manually enter a pgp keyphrase, you can be additionally assured that even if someone got hold of your keyrings, they would not be able to sign your signature. |
Channel Keyphrase - The main purpose of MPGP is to create and exchange channel keys for mircryption encryption of channels.
| • | If you invoke the MPGP dialog on a cannel with an existing mircryption key, it will be displayed in the contents box. This is for sending an existing key to someone who doesn't have it. You can also change the key in this box. When you send a changed key, it will change the key on your local mirc automatically. You will receive a confirmation when the recipient has accepted the new channel key and it is safe to use. |
| • | If the current channel has no existing mircryption key, a long cryptographically secure random key will be generated for you with the [RAND] prefix. You can (re)randomize the current channel key by right-clicking in the channel keyphrase window. |
Stored Public Key - You can send non-anonymous (permanent) public keys to other people using mpgp, in order to share the public keys for yourself or other people.
| • | When sending public keys, note that you will never be sending the private component of a key, which is used to decrypt messages, only the public component which allows messages to be encrypted to that person. |
| • | However, typically you want to be wary about accepting public keys from people you dont know, because if you later find the key on your public keyring, you may forget who you got it from and think that you can trust that the person/email it refers to is trustworthy. In other words, if a stranger send you a public key for "Bill Clinton", it does not nescesarily mean that that key corresponds to bill clinton, and you dont want to forget that. PGP in fact has an entire system of assigning trusts to keys which you can access through the Key tool. |
| • | You also probably want to be wary about sending your friend's public keys to people without their permission, or they will be surprised that someone has the ability to send them encrypted messages when they never gave their key to that person. |
| • | Lastly, public keys sent to a recipient using their anonymous key is technically susceptible to a man-in-the-middle attack in the same way as messages are. But because once a public key is accepted it could be used in future authentifications, and because these public key exchanges occur over irc and not an outside channel, you should be doubly paranoid about accepting public keys that are sent to your anonymous key or not signed with a trusted key. |
| • | In general, you should only accept public keys that are sent to and from non-anonymous keys you trust. |
Text Message - Just send a brief text message.
| • | Normally to have a secure conversation you would open a channel or query window with another person and exchange a mircryption channel key. Using mircryption to encrypt channel/query conversations takes up minimal extra bandwidth and can be used for real-time encrypted conversations, and mpgp has a right-click menu for making it easy to open such conversations. |
| • | However, there may be times when you just want to send someone a brief one-time message without opening up a channel/query for extended conversation. |
File - send a single file to the recipient, encrypted and compressed.
| • | Select this option, open up your windows explorer, and drag a single file into the Contents box. Before sending, this file will be encrypted and compressed. |
| • | Note this is an extremely slow process, because, unlike normaly dcc file exchange, the transmission of the file is sent entriely over normal irc bandwidth, through any bnc or proxy. On a recent test, we transferred a 33k file in 11minutes, which comes to about 50 bytes per second. So basically we've gone back in time to the technology one step prior to the acoustic modems where you pressed your handset into the rubber suction cups when the other line started squealing. |
| • | You should only use the mpgp file sending feature if you one of the parties is using a bnc/proxy and does not want to reveal their true ip to the other person. If neither party is connected through a bnc, then you should use the buit-in mirc file transfer system, and encrypt the file using an external product (such a pgp), which will be 100x faster to transmit. |
|
